 |  |
by Bernard B. Spindel
with Bill Davidson
I'm a wiretapper. I'm also an electronic eavesdropper. I practice an art which has progressed so far in the last 10 years that few people, if any, are entirely safe from the prying ears of snoopers like me. If someone wants to know badly enough what you're doing and saying, and is willing to spare no expense to find out, there's no place to hide-unless you build specially designed secret rooms costing probably hundreds of thousands of dollars.
So much progress has been made in electronic eavesdropping that I personally believe an expert-given sufficient funds-could wiretap the White House despite all the elaborate precautions of the Communications Security Staff of the U.S. Secret Service. It would be far easier to learn the secrets of a congressman (as I recently demonstrated to a Congressional committee).
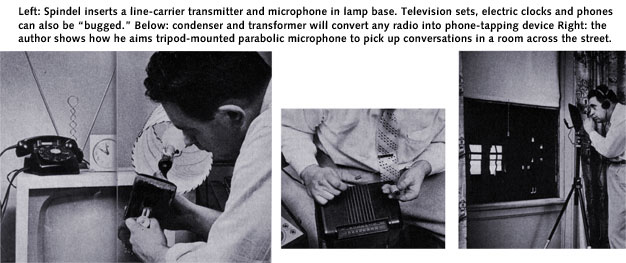
Legislative committees and grand juries have called author Spindel for expert testimony on electronic eavesdropping apparatus. Here he taps a telephone line at cross box in basement
|
|
A wiretapper need only sit in the legislator's anteroom as though waiting for an appointment. With a small induction coil in his pocket, he could pick up the congressman's telephone conversations from the line leading to his receptionist's extension. The coil would feed into a tiny earphone, disguised as a hearing aid, and if the expert wished, he could record the conversations on a miniature recording machine concealed in a shoulder holster under his jacket. If the congressman were suspicious and did not reveal anything on his office phone, the expert could follow him to a pay phone. There he could use a more powerful induction-coil device to listen to and record the congressman's conversation.
I have used all these devices-and many more. I have tapped telephone wires with new techniques so undetectable that I have recordings of telephone-company officials checking the lines and phoning the tappee to tell him that tests had revealed no interception. I have photographed adulterous lovers in total darkness without their knowing it, and recorded every word of their conversation with the aid of tiny radio transmitters the size of a pack of cigarettes. I have penetrated electronically a fortresslike trysting place so heavily guarded that it would have taken a company of infantry to break in. Using hidden microphones, I have helped save union leaders from murder and business officials from fraud and blackmail.
 Abuses of Electronic Eavesdropping
But I'm not proud of my achievements in electronic eavesdropping. I've seen too many people injured without a fair trial, too many abuses of these new techniques by unscrupulous police and a small handful of corrupt telephone-company employees. (The professional honesty of the vast majority of telephone workers has never been questioned.) I've seen the technical advances which make possible a wholesale invasion of the right of privacy of American citizens as guaranteed in Article IV of the Bill of Rights of the Constitution. Although I limit my business to legal wiretaps (if I wanted to take illegal jobs, I could earn upwards of $200,000 a year), there are so many loopholes in the law that electronic listening devices can be dangerous weapons in anyone's hands. They can go off at any time to wreck innocent lives.

Who am I to speak out on such a complicated constitutional subject? I have been a private detective (licensed), and I am one of the country's dozen-or-so wiretap technicians (no license required) who are hired by other private detectives to do their electronic snooping. I have designed some of the equipment in use today. I've testified as an expert witness before Congressional committees, state legislative bodies and grand juries. I have told them that stringent safeguards must be written into the wiretapping and eavesdropping laws-even if it means legislating me out of business. I have used cases from my own files to show how power-hungry officials could make this country a nightmare super police state such as that visualized by George Orwell in his book, 1984. Already some government officials are spying electronically on subordinates, some businesses are spying on competing firms, some unions are spying on rival unions, and anyone can have a peep-show view of anyone else's life.
If these statements sound fantastic and unnecessarily alarming, just consult your daily newspaper. Only a few weeks ago the press carried page-one stories about a New York City wire-tapping ring that set up elaborate listening posts in two East Side apartments to monitor the telephones of assorted business firms and individuals. Two telephone-company technicians-since discharged-were accused of making certain technical adjustments in a nearby telephone exchange building to enable the listening posts to eavesdrop on any of the 56,000 lines served by the building. A cable capable of carrying up to 100 calls simultaneously led from one of the apartments to the telephone building. The ring operated for a year and a half before a police raid forced it to cease operations.
Indicted as mastermind of the setup was John G. (Steve) Broady, a New York attorney and private investigator. He was accused specifically of having tapped 14 telephones in the names of eight persons and corporations on four different exchanges. The indictment said those whose phones were monitored included Ethelbert Warfield, former law partner of New York City Police Commissioner Francis W.H. Adams; the Knoedler Art Galleries; the pharmaceutical firm of E.R. Squibb & Sons; the wife of an investment banker involved in divorce proceedings, and two models. Broady had had a previous brush with the law over wiretapping. In 1949 he was indicted with two other private investigators on charges of tapping the telephones of New York City officials, including the then mayor, William O'Dwyer. The indictment subsequently was dismissed.
Let me tell you, too, about some of the 70 or so routine cases I handle every year. All point up the ease with which someone can eavesdrop electronically on you without your knowledge.
Not long ago, I was called in on an Alabama case involving the president of a metal products company. The executive's wife suspected he was philandering, but she had not been able to get proof. My first move was to install a wiretap on her phone. (In 32 states, it's legal to tap your own phone.) The tap was easy. The executive and his wife lived in a big house in the suburbs. Posing as a telephone repairman, I climbed a pole outside their house and noted the identifying number of the pair of wires leading to their telephone. The wires fed into a cable containing the wires of many other telephones in the neighborhood.
I followed the cable to an "appearance," or bridging point, three miles away. There the cable joined several others. I found the executive's telephone wires again and hooked to them another pair of wires leading to a room I had rented nearby. I could sit there in comfort and record every conversation on the executive's line.
The very first night the pattern became clear. The executive phoned a young woman he called Mary Ellen and arranged to meet her the next evening in his office. His wife told me that he often stayed at his office until ten or eleven at night.
I checked the office; it was a veritable fortress protected by a private alarm service and three heavy oak doors which were locked and bolted at night. Also, according to the wife, the executive had spent thousands of dollars to make his office microphone-proof-on the pretext that his competitors might try to plant bugs, as we call hidden microphones, to learn his trade secrets (a practice which is legal in most states).
Baiting a Trap for an Erring Husband
I decided to use a Trojan-horse ruse. I told the wife to buy her husband a combination radio, television set, phonograph and bar for his office. The handsome piece of furniture cost $650, and I had a use for it. Among my eavesdropping gadgets is a miniature transmitter, only slightly larger than a book of matches. It has a built-in microphone and sends its signals over conventional electric power lines. I concealed the transmitter in the speaker of the radio. The moment the executive plugged his handsome new gift into the electric outlet, I could hear every word spoken in his office. I listened through a receiver plugged into an electric outlet in a vacant store which I had rented a block away.
My signal was drowned out when the executive played the set, but fortunately there were times when he was interested in other activities. In two weeks, I obtained three good recordings containing evidence of adultery-and more besides. The husband bragged to his girl friend about assets he had concealed from his wife. "Take this check I'm making out for you," he said to Mary Ellen. "It's drawn on a California bank and my wife doesn't even dream that I have an account there." Not only did the wife get her divorce, but in a quick settlement out of court she also got a share of the money and property she didn't even know existed.
If you think such electronic eavesdropping occurs only in big cities, let me tell you what happened in 1949 in a small Midwestern town. I was called in by a hardware jobber who handled expensive tools and dies. He had suspected that his partner was cheating him, and a study of the books one weekend revealed that $40,000 worth of material was missing. I was hired to find out what was going on.
I installed a wiretap at the hardwareman's switchboard and listened in at a "plant" (listening post) in the basement of an empty building four blocks away. Again I got the key evidence the first day.
The partner's telephone calls revealed that he was shipping the missing goods to a secret warehouse, then selling some of them on his own and storing the rest so as to have an adequate stock to start an independent business. He was planning to break up the partnership.
Parabolic Microphone on a Truck
But we still didn't know the location of the warehouse and who was receiving the stolen goods-so I reached deeper into the bag of electronic tricks. One day I drove up to my client's establishment in a truck bearing a fake name, "Bates Sound Service," and parked across the street. In the truck was a gadget mounted on a tripod and aimed through an opening covered with thin black muslin. The device was my own version of a parabolic microphone, a sensitive, dish-shaped "ear" which radio and TV stations use to pick up the voices of cheerleaders hundreds of feet away across a crowded football stadium.
I knew from the wiretaps that during the morning the wayward partner would often say he was going out for coffee, but usually he would meet a man in a car in front of the hardware company. On this particular day, he left the building precisely at 10:30 a.m. and got into the waiting car. It was warm and the car windows were open. The partner pulled out a sheaf of papers and began to talk to the driver. In my truck across the street, I aimed the concealed parabolic microphone at an open window of the car, and began to record the conversation. It came over as clearly as though the two men were talking in the same room with me-and the dialogue was interrupted briefly only when passing trucks drove across my line of sight. The partner was discussing bills of sale for his illicit side business. The driver of the car was his deliveryman. In 15 minutes I learned the location of the warehouse and the names of most of the customers for the stolen goods.
Two days later my client and I called in the partner and informed him that we knew what he was up to. I recounted the details. "You're a liar," he shouted. "Okay," said my client, "then let's listen to some recordings." The wayward partner listened and turned pale. "I don't want to send you and your friends to jail," said my client. "All I want is an amicable settlement of the partnership." Two weeks later the partnership was dissolved. Not only did the larcenous partner have to pay for all the stolen merchandise-but he paid my $3,000 fee.
A recent case of what might be called political intelligence provides another example of my techniques. I was hired by a private organization to try to get information about a group in New York called the National Renaissance party, which the House Committee on Un-American Activities has cited as a Fascist organization. A contact who had managed to become a member of the party had arranged for an important meeting to be held one night in his uptown apartment. He sneaked me into his apartment the day of the meeting and in a few minutes I converted a telephone into a live microphone which picked up every sound in the room, even when the phone was on the hook. Using spare telephone lines, I then connected the bugged telephone to a tape recorder disguised as a piece of luggage. I hid the recorder under the tenant's bed, among half a dozen other suitcases.
The meeting took place that night as scheduled, and we obtained some amazing recordings. One speaker extolled the late Adolf Hitler as a great man. "Hitler made one mistake which led to his downfall," the speaker said, "and we must avoid that mistake-concentrating on too many objectives at once." In the course of the evening, we got confirmation of some of the party's plans and of the identity of its principal backers. I turned over the recording to the organization that had hired me. It was preparing a report for the House committee.
In all these cases, my electronic eavesdropping was legal and attained desirable objectives. Just think, however, how the same equipment could be used in other ways. Various Congressional investigations have revealed that a Rhode Island governor, William H. Vanderbilt, had the wires of Republican and Democratic adversaries tapped; that a Pennsylvania state senator listened in on the phones of Philadelphia's then mayor, S. Davis Wilson; and that a Washington, D.C., police lieutenant named Joseph W. Shimon on a private job wire-tapped the executives of an airline. Of this last case, a Senate report said: "Your subcommittee is impressed by the ease with which unauthorized persons, such as Lieutenant Shimon, can invade the privacy of telephone conversations."
One of the most shocking abuses of wiretapping came to light in 1953, when Brooklyn District Attorney Miles McDonald told a subcommittee of the House Judiciary Committee: "We found in the course of our investigation in the Harry Gross [bookmaking and police bribery] case that the police officers were buying their own wiretapping equipment. They would sit in on a telephone such as a coin booth near a baseball park or near a race track, and when they heard people call up to make a bet they would forward that to another plain-clothes detective, who would then go and shake that bookmaker down."
Oil-Company Geologist's Phone Tapped
In Texas, a wiretapper (now dead) admitted to reporters that he had made a small fortune by tapping the phone of an oil-company geologist, then reporting the expert's findings to a land speculator who paid handsomely for the information. And it is well known in political circles that a former governor of a big state had several police wiretap experts on his personal staff listen in on the phones of his principal subordinates as well as those of his political foes. The system backfired, however, when a recording was played for him and he heard a voice say, "And I don't give a damn whether or not the miserable so-and-so-------is listening to this."
Serge Rubinstein, the sinister international financier who was murdered in New York City a few months ago, was devoted to the use of electronic eavesdropping devices. He even bragged he had pulled off business coups after illegally tapping the wires of his competitors. He called the tapped material business intelligence.
The Rubinstein murder investigation revealed that the financier also had made other uses of eavesdropping equipment. He had got hold of a tiny, powerful, battery-operated radio transmitter, which was supposed to be manufactured for use only by law-enforcement agencies. (New York's Anti-Crime Committee determined that Rubinstein got the device from a wiretap technician, who got it from a private detective, who got it from a New Jersey police department.)
The transmitter would operate on its batteries for 10 days, and it could be installed as easily as screwing in an electric-light bulb. Rubinstein hooked the transmitter under the springs of the bed of a woman friend named Pat Wray. A private detective sat in a parked car a block away with a radio receiver and a recorder. After the story leaked to the newspapers, Miss Wray was quoted as making the classic remark, "I guess everyone now knows my bed squeaks."
Altogether, nearly a dozen manufacturers are producing electronic snooping devices, mostly for law-enforcement agencies. However, I design many of my own. For tapping phones, I have a device which enable me to find one pair of telephone wires in a jungle of hundreds of others-even though the lines are not numbered or identified in any way. The device has 36 tiny neon bulbs in it. From each bulb runs a pair of wires tipped with clips. I attach the clips to 36 terminal pairs at a time in the "cross box," in the basement of the building in which the phone I want to tap is located. (All telephone lines in a building run into a cross box and from there are fed into an outgoing cable.) When I dial the number of the phone I am seeking, one neon bulb will light up, identifying the pair of wires I'm looking for. I follow those wires to the next bridging point many blocks away and set up my plant in a basement or vacant apartment nearby.
In the plant itself, I use special recording machines which I design and construct. My recorders operate for 13 hours without requiring a change of tape. They can be equipped with a gadget which punches out telephone numbers as the tappee dials them. They also have a device, designed by me, which turns them on only when the telephone is lifted from the receiver.
For hidden microphone jobs, I have other devices to start and stop the recording equipment. I conceal these tiny gadgets in a light fixture or lamp. The gadgets all have an extremely sensitive circuit which is activated by the sound of the human voice. Without such a circuit, the recorder would have to operate 24 hours a day.
The voice activator turns the machine on (even though the recorder may be in a plant many miles away) when human voices are talking in the bugged room; the same device turns the recorder off after the conversation ceases. Some of these voice activators transmit their signals over power lines; for others, I may rig my own wires between the bug and the voice-activated recorder. Where it is impossible to run wires out of the building, I use TV antenna wires that go to the roof. There I have a specially housed electric bulb (called an exciter lamp) that emits invisible infrared rays when it receives an impulse from the microphone in the room below. When a person talks in the room, the rays beam across the street to another roof where a photoelectric cell picks them up. This "electric eye" sends the signal over wires to the plant-and the recorder starts operating.
The infrared ray is one of my most valuable weapons. I have special infrared flash bulbs and infrared photographic film to take pictures in total darkness. The flash bulbs give off no more warning light than an instantaneous glow the size of the tip of a lighted cigarette. Time after time, I have photographed adulterous lovers in the moment it took me to drive past their parked cars-or through windows they had left open in the belief that darkness was their ally.
Phone Booth Doesn't Ensure Privacy
I make my own induction coils, some of which are so sensitive and directional that with them I can pick up a conversation in a telephone booth from many feet away while pretending to shop or study a telephone directory. (The standard commercial induction coil must be placed directly under the phone in order to intercept the magnetic field of the electric current carrying the voice impulses.) To record such conversations, I sometimes use a ware recorder the size of a paper book, which can be carried in a shoulder holster or in a pocket. If I am in a public place and want to tap a line with an induction coil and listen in directly without anyone spotting me, I use a powerful pocket amplifier with an earphone that looks like an ordinary hearing-aid earpiece.
Using tiny printed circuits and miniature tubes or transistors the size of a pencil eraser, I also construct "line-carrier transmitters" no bigger than a cigarette lighter. These can be concealed in electric sockets, in electric clocks or picture moldings, and they accurately transmit the human voice over power lines. In most cities an entire block is fed by the same power line, so I can pick up the signal anywhere in the block-as I did in the Case of the Wayward Alabama Executive-simply by plugging a receiving set into any electric outlet.
The line-carrier transmitter works on the same principle as the wireless interoffice or "baby-sitter" intercom system you can buy in any appliance store for about $30. The only difference is that my transmitters must be reduced to the smallest possible size.
When I can't get into a room to install a line transmitter or a proper microphone (some of my most sensitive bugs are no bigger than a dime and can be flush-mounted in a wall), I use miniature radio transmitters such as the one that Rubinstein hooked onto his girl friend's bedsprings. These tiny transmitters come in three types and are manufactured commercially for law-enforcement agencies. I make my own. The smallest of the three commercial models is a battery-operated type the size of a pack of cigarettes. It runs for 12 to 24 hours. The second is the slightly larger external battery-pack type used by Rubinstein. It transmits for as long as 10 days. The third type operates on house current and runs for months-until the parts burn out.
All three types are simple to use. You merely press a button to start them transmitting. They have a range of up to two miles-depending on the location, the power and the frequency. I have dropped them into cars, slipped them into hotel rooms in vases of flowers, smuggled them into offices in brief cases left behind "by mistake."
Another modern method of eavesdropping on an inaccessible room is to use a contact microphone, which picks up sound by resonance. If I drive a nail through a wall and attach a contact mike to the nail, the microphone will faithfully reproduce the voices through the wall. In one case in Ohio, I had to know quickly what was going on in an art studio in which my client's wife was entertaining a man supposed to be her cousin. On a hunch, I attached a contact microphone to a plate-glass picture window. The glass acted as a resonating surface and the contact mike picked up every word said inside.
If I can get into a room to do the actual bugging, the job is easy-especially if there is a telephone. I have learned from long experience that the mouthpiece of the standard telephone is one of the most effective, most unsuspected eavesdropping microphones ever invented. Entering a house in the guise of a telephone repairman checking the instrument, I can replace the standard two- or three-wire line from the telephone to the wall connection with a special three- or four-wire line. The whole job takes only three or four minutes-and after that the telephone mouthpiece will pick up all conversation within 30 feet and transmit it over the telephone lines, even if the phone is on the hook.
For this type of bugging, I set up my plant the same way I would a wiretap. I trace the subject's telephone lines to a bridging point and connect them with another pair of wires leading to the plant. I can listen in from several miles away, or even in another office in the same building-as I demonstrated to the staff of Collier's a few weeks ago.
To me, the most dangerous of the new electronic eavesdropping devices are those that pick up human voices without any wires or transmitters whatever. Chief among these instruments in current use is the parabolic microphone, which radio and TV networks use at President Eisenhower's press conferences to pick up his voice from the rear of the room-and which I employed in the Case of the Larcenous Hardware Jobber. True, the effectiveness of the parabolic microphone is limited by line of unobstructed sight; if a closed window, a heavy curtain, or even the body of another person comes between the subject and the microphone, conversation cannot be heard. But even so, the device is devilishly effective.
The "dish" or "ear" of the broadcasting companies' parabolic microphone is a cumbersome object about three feet in diameter. As it points at its target, it looks like a huge cereal bowl standing on end. I have a less obtrusive model which uses a smaller dish. It is so sensitive and selective that I aim it with a gun sight equipped with an eight-power telescope; unless it is zeroed in directly on the subject I lose contact. I have used it to eavesdrop on lovers who thought they were safe on lonely park benches and in parked cars. But my most unusual use of the instrument was in another kind of case. One of my clients was asked to meet a suspected shakedown artist on a New Jersey beach. The alleged blackmailer demanded that my client, like himself, wear only a bathing suit so that no recording machine could be concealed on his person, but the precaution was in vain. Not a word of the conversation escaped the parabolic microphone hidden in my truck on a nearby hill. When my client let it be known that he had recordings of the conversation, the would-be blackmailer stopped bothering him.
The parabolic microphone and other devices I have described-plus some still secret-are the reasons why I say that even the White House may not be completely safe from the electronic eavesdropper. Such high-level eavesdropping would be difficult, of course, because of the vigilance of the Secret Service, but nevertheless it is within the realm of possibility. Defense against an expert wiretapper is most difficult. The telephone exchange handling the White House is carefully watched by the Secret Service, but so many technicians work in and around an exchange that just one dishonest or disloyal employee conceivably could run a still-secret type of invisible connection from the White House wires in the course of his normal work without being spotted. Then a plant could be set up 10 or 50 miles away, and looking for it would be like searching for the proverbial needle in a haystack.
Then, too, the cable from the White House runs underground for a considerable distance. There always are men working near it, servicing power lines, cleaning sewers or digging in basements and excavations. If a wire tapper could get to the cable for just a few minutes (perhaps even buying a nearby building to do so), he would need only to cut into the cable and run six inches of wire off the President's line. Then he could place an induction coil near the added wire, run his connections back to the adjacent building and bury the cable and the coil in the earth again. There would be no physical connection with the cable, and there is no known way of detecting the presence of an induction coil.
Greatest Risk Is as the Receiving End
There's an excellent chance that the ever-alert Secret Service would thwart any such plots in the vicinity of the White House. But remember there is almost half a mile of cable between the White House and the telephone exchange. Also, it's possible to tap the unguarded wires of persons receiving calls from the President-perhaps 3,000 miles away.
The government's top-secret cables would also be vulnerable to an expert wiretapper. There are ways to circumvent the warning and protective devices with which they are fitted. One type of cable, for example, is filled with compressed air. The moment the cable is opened, the air pressure drops, setting off an alarm. There is an eavesdropping device, however, which fits around the cable and permits only a negligible amount of air to escape into a cup. For jobs taking long periods of time, pressure can be fed into the cable to compensate for any air that may escape.
Other top-secret cables are wrapped in a special winding which constantly transmits a high whining sound. It's like a radio-jammed signal, and it's designed to foil induction-coil pickups. To circumvent it, an expert would record the conversations passing through the cable-along with the jamming-and later use special electronic equipment to filter out the jamming.
Sometimes an important official conversation is scrambled and split up electronically; half of it is transmitted by radio and the other half by telephone line. This technique, too, is designed to foil the wiretapper, who would get only a meaningless jumble of sound if he eavesdropped on the cable. But it's always possible to intercept a radio signal, and if you can obtain either the radioed or telephoned half of the conversation, there is electronic equipment that can fill in the missing half and give you the complete conversation.
All in all, the offense has been able to keep ahead of the defense in this ultraserious business of electronic eavesdropping. Is there any defense at all? I'll discuss that in my article in the next issue.
Meantime, I can only say that I practice one important defense tactic in my own home. I don't own a telephone. Such a drastic step isn't necessary for most Americans; it's inconvenient, and the average person is rarely involved in matters that others would pay money to learn about. But since I am a wiretapper-and a target for snooping-it is the only way I know to keep others from prying into my professional secrets.
|







